The term “roaming” is widely used to describe the process of switching between Access Points. In this context, an STA (Station) associated with AP-A transitions to AP-B based on criteria such as RSSI, channel occupancy, and other factors.
In the context of Wireless Internet Service Providers (WISPs), “roaming” refers to the use of a network to which the subscriber has no direct contractual relationship. For example, a user subscribes to a WiFi plan with Provider A but can access the service through Provider B’s network.
According to the WBA definition, we have:
“Wi-Fi Roaming is a service provided by a network provider/operator to end users/device owners who are not customers of that company. ” WBA – WRIX Umbrella
In the example above, the user is able to access the network through the provider without having a contractual relationship with the visited network provider.
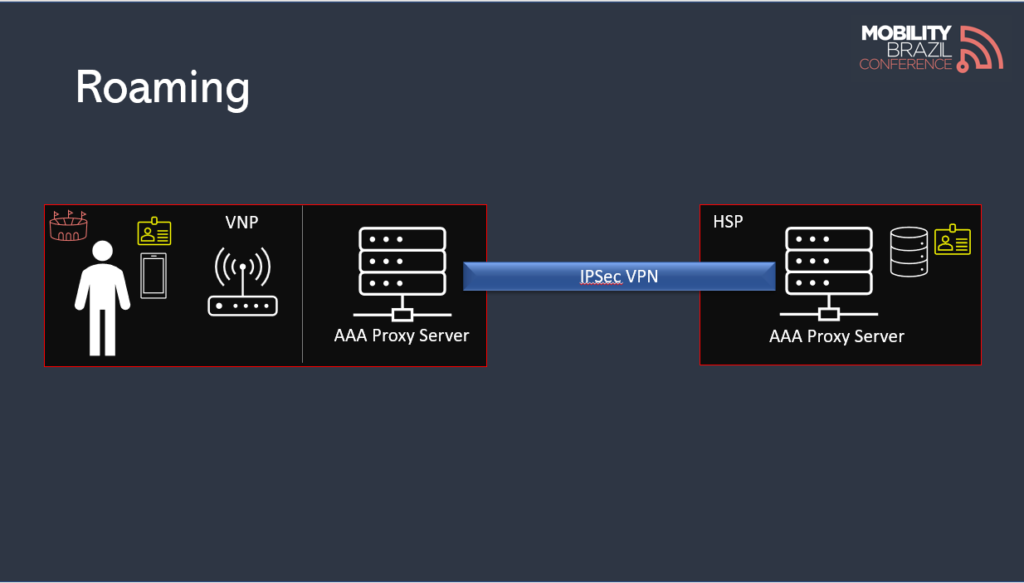
HSP (Home Service Provider) is the network to which the user has a subscription, while VNP (Visited Network Provider) is the network where the subscriber uses services without having a contract.
For this type of connection to be possible, the VNP must have a way to authenticate users. Therefore, the VNP and HSP require some form of interconnection.
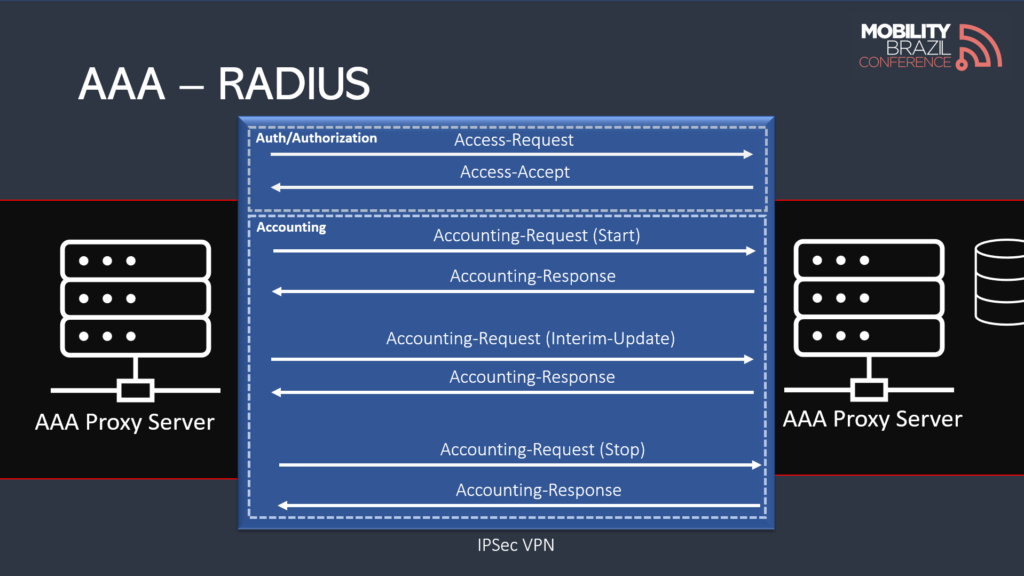
The most common method for exchanging authentication data is through the AAA framework, implemented using the RADIUS protocol.
RADIUS is a protocol within the TCP/IP stack that uses port 1812 for authentication and port 1813 for accounting. Some fields in RADIUS messages are transmitted in plain text, while others are encrypted.
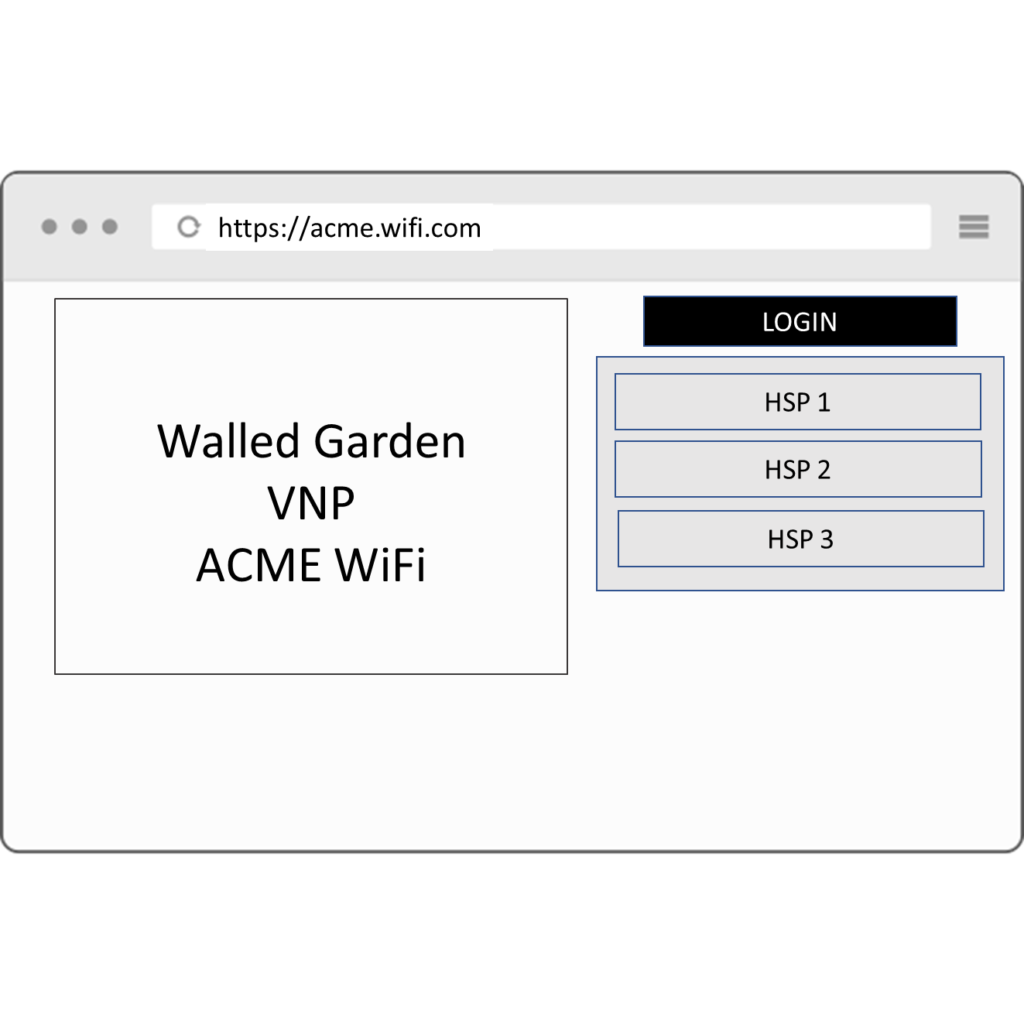
Roaming on an Open Network via a Captive Portal
The user connects to an SSID, typically open, with the connection limited to a few protocols such as DNS and HTTPS for the captive portal. When the user attempts to access any webpage using a browser, they are redirected to the VNP’s portal. Typically, the user must manually select their HSP from a list.
RFC 7710, the Captive-Portal Dynamic Host Configuration Protocol Relay Agent DHCP/RA option, aims to allow devices to become aware of the presence of a portal via DHCP, thus enabling the future implementation of standardized mechanisms.
It is important to note that this type of access creates usability challenges. Initially, the user must identify the SSID they should connect to, which has a roaming agreement with their VNP.
Next, the user must manually select their HSP.
Open Network – WISPr
WISPr is a specification created to facilitate access. Pages that are compatible with WISPr include information about partners and how authentication should be carried out within their captive portal. WISPr allows for some standardization of Smart Clients, which are apps that enable Wi-Fi network connections. However, it still doesn’t address the issue of lacking encryption, isn’t widely standardized, and doesn’t allow for network identification before the user connects.
Web Login/WISPr Challenges
Security alerts/issues with HTTPS redirection.
- Identifying the correct SSID;
- Proprietary portal identification mechanisms;
- The network typically lacks encryption;
A common issue with captive portals is that each vendor implements detection mechanisms differently, leading to an inconsistent user experience. A significant improvement comes from adopting standardized methods. The CAPPORT (Captive Portal Interaction) working group introduced RFC 8910, which proposes a standard where the captive portal URL is conveyed through a DHCP option field, streamlining the process and ensuring a more predictable experience for users.
Hotspot 2.0
Hotspot 2.0 is a technical specification developed by the Wi-Fi Alliance to improve the connection experience on Wi-Fi networks automatically and securely. It is based on the 802.11u, 802.11i, and 802.1x standards.
The Passpoint certification program was created for devices that meet Hotspot 2.0 specifications. The term “Passpoint” came to refer to the technical specification itself, and the term “Hotspot 2.0” is no longer in use.
IEEE 802.11u
The 802.11u is a very important part of the Passpoint specification, allowing STAs (Wi-Fi clients) to have network-related information (Layer 3) before associating with the SSID. This includes knowing if the network has Internet, a public or private IP (NAT), mobile operator lists, domains, etc.
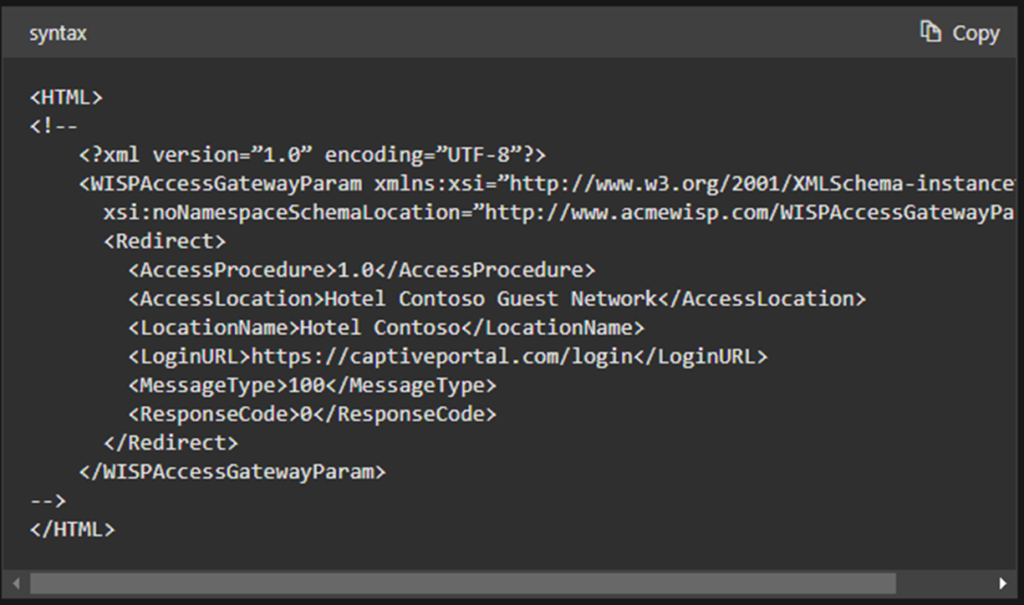
ANQP
For requesting added information, most implementations use ANQP (Access Network Query Protocol), which is transported via a protocol called GAS (Generic Advertisement Service).
Below is the list of ANQP elements. All of this information can be gathered by the device prior to associating with the 802.11 network!
Reference: https://higherlogicdownload.s3.amazonaws.com/HPE/MigratedAttachments/63AF17E3-09CD-4369-A476-CD91D4FA888B-1-WP_PasspointWiFi_062912.pdf

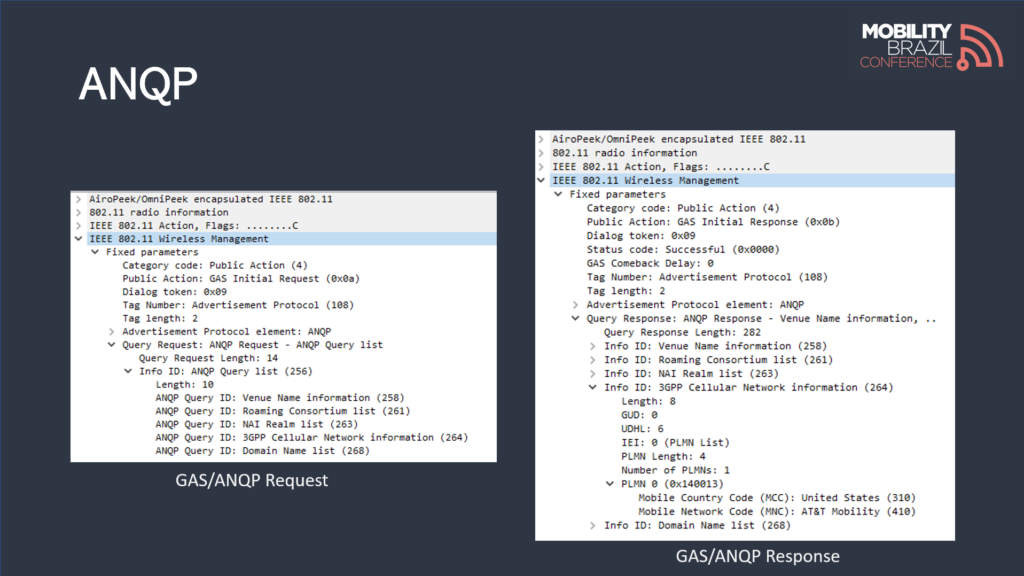
Passpoint supports EAP methods that enable authentication via certificates, SIM/eSIM, and user credentials (username and password).
Passpoint Releases
- Release 1: Network discovery and security.
- Release 2: Added Online Signup and Policy Provision.
- Release 3: Terms of use acceptance, new ANQP elements, and a single SSID for registration.
Passpoint was launched in several phases, initially allowing automatic discovery and connection. In subsequent phases, methods for user onboarding through registration and provisioning of the Passpoint profile were added.
Onboarding:
- Operators can sell devices with the Passpoint profile pre-installed.
- Proprietary apps can install the Passpoint profile.
- Passpoint profile installed via app or OTA (over-the-air).
VNP-HSP Interconnection: Key Considerations and How WRIX Helps
For VNPs to allow user access, a mediation (proxy) system with the HSP is required. This interconnection raises several key considerations:
- Data Validation: Ensuring accurate and secure data exchange between VNP and HSP.
- Interconnection Standards: Establishing technical standards for interoperability between networks.
- Billing Methods: Defining how VNPs charge HSPs and users for roaming services.
- Security Recommendations: Implementing secure data exchange protocols and authentication measures.
How WRIX Helps: The Wireless Roaming Intermediary eXchange (WRIX), developed by WBA, provides a standardized framework that addresses these challenges. WRIX ensures smooth interconnection, data validation, security, and billing, simplifying the roaming process for VNPs and HSPs while ensuring compliance with global standards.
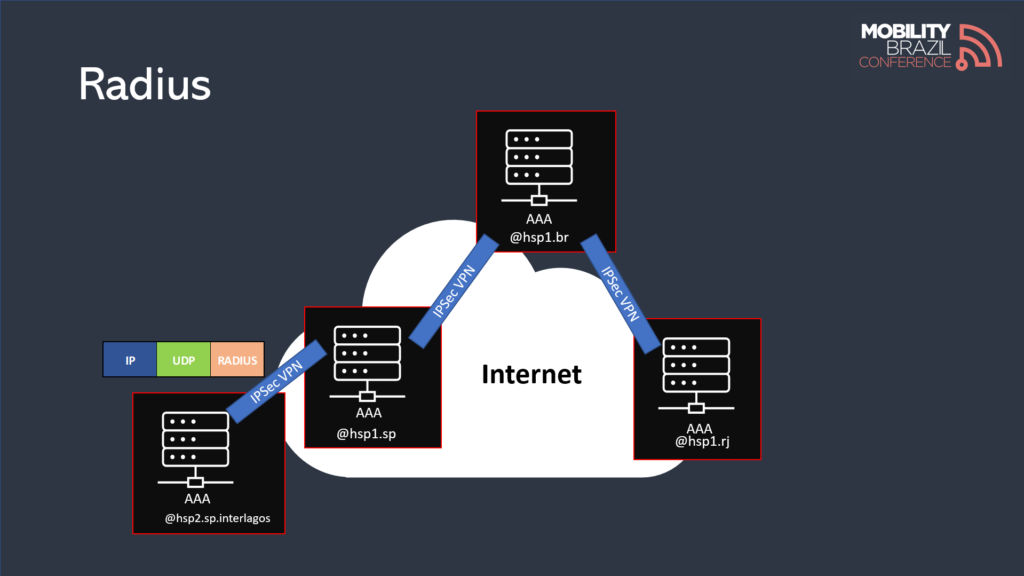
Radius Hierarchy
It is common to deploy Radius servers following a hierarchy, as shown in the figure below.
This type of architecture can introduce several intermediate hops, depending on how the hierarchy is structured.
The figure below illustrates an example of a hierarchical Radius architecture, where we can observe that the number of intermediate hops has increased. For each hop, it’s important to remember that packet routing, encryption, and other processing operations will occur, leading to an increase in latency.
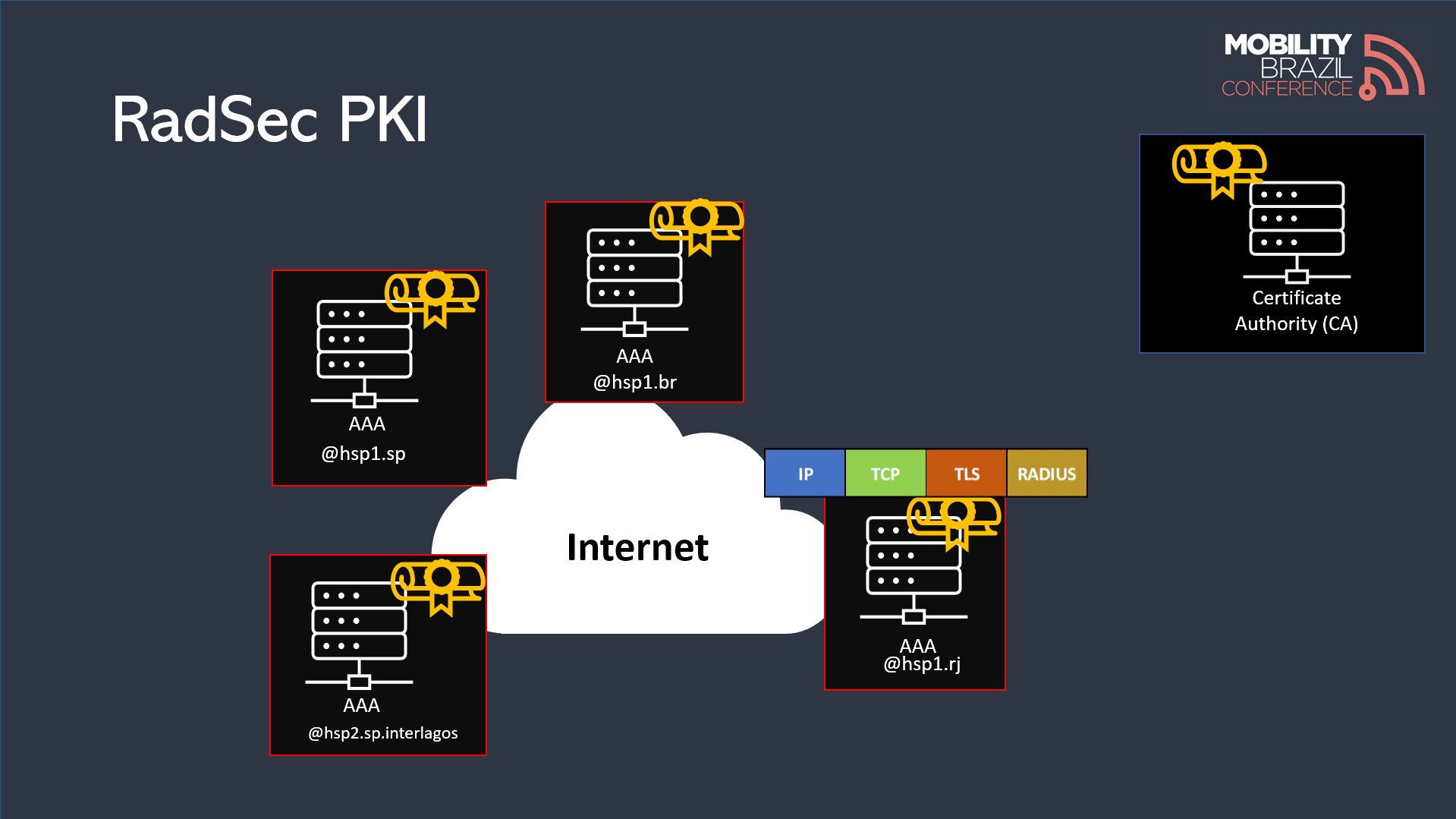
RadSec
RFC 6614 proposes the use of TLS encryption for Radius, ensuring that messages are fully encrypted. Additionally, RadSec is deployed using TCP, which consolidates the communication to a single port instead of the traditional two-port setup.
This approach enhances security by encrypting all Radius traffic, preventing sensitive data from being transmitted in plaintext. Moreover, by utilizing TCP and a single port, RadSec simplifies network configuration and can improve reliability, as TCP guarantees message delivery and ensures better handling of packet loss compared to UDP, the traditional transport protocol used in Radius.
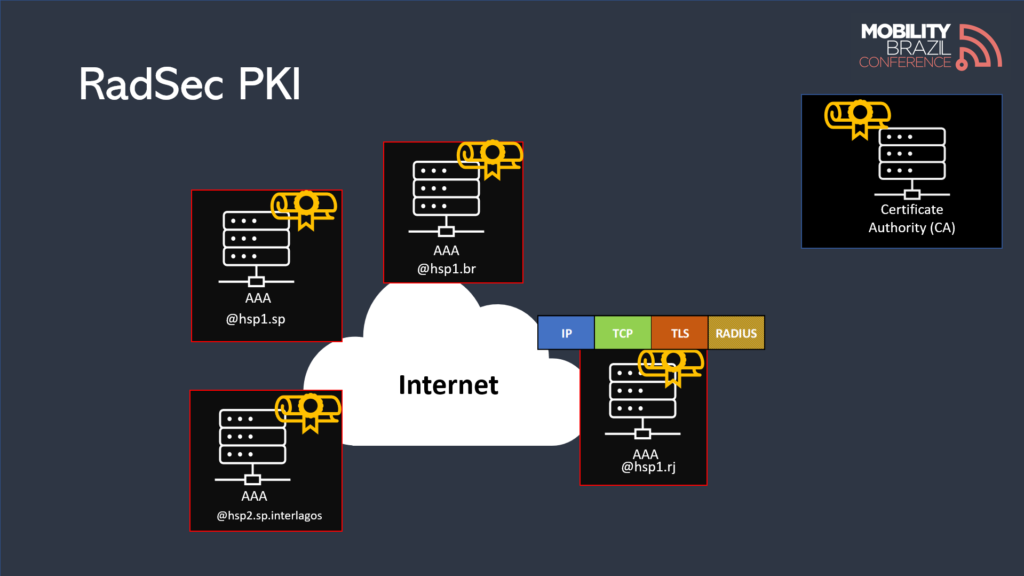
Eduroam
Eduroam is an excellent example of a federated Radius network that uses WPA2 Enterprise.
RFC 7593 provides a detailed overview of the challenges, technical decisions, and architectures employed by the project.
Eduroam can be considered a predecessor to OpenRoaming. It is based on the use of Radius with TLS (RadSec), where federation members have X.509 certificates issued by a Certificate Authority (CA).
Discovery of Radius Servers
Since Radius servers may now be exposed directly to an untrusted environment like the Internet, a dynamic method of server discovery is necessary. This ensures a more efficient communication process with fewer hops between servers.
Eduroam addresses this challenge through a dynamic discovery method using DNS queries with NAPTR/SRV records. This dynamic approach allows for the efficient location and communication between servers, reducing the need for static configurations and improving network resilience.
Open Roaming
Finally, we arrive at the last section where I’ll talk about Open Roaming. In fact, you will see that the key components have already been described, and now we will simply piece them together.
Open Roaming was developed by Cisco and introduced to the public in 2019 with the goal of providing seamless roaming between Wi-Fi 6 and 5G.

The architecture is based on Access Providers and Identity Providers (https://www.cisco.com/c/en/us/solutions/collateral/enterprise-networks/802-11ax-solution/nb-06-open-roam-seam-aag-cte-en.html)
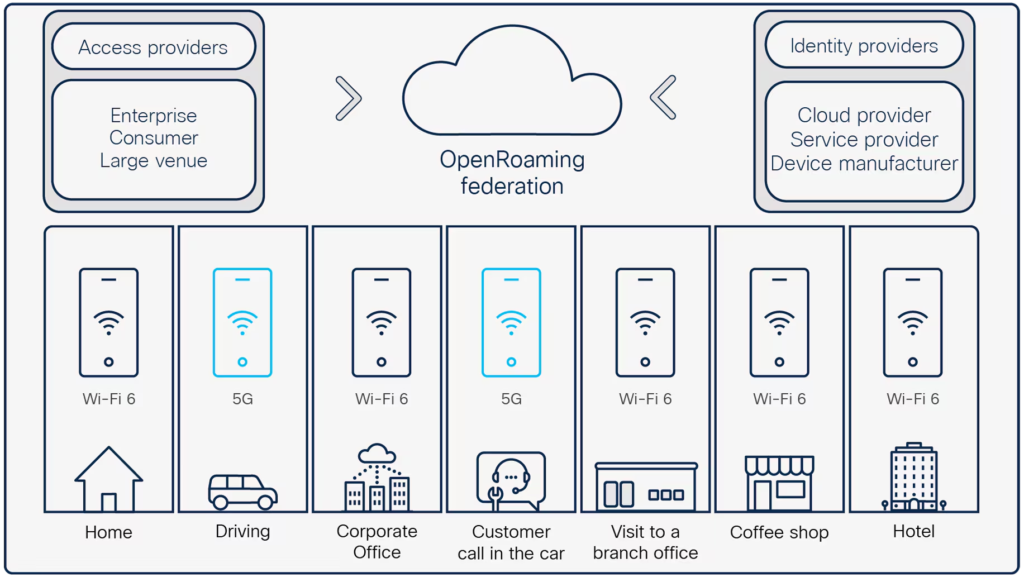
Access Providers are companies that own Wi-Fi infrastructure in both public and private places such as airports, stadiums, and public squares.
Identity Providers are responsible for maintaining the user database, such as telecom operators, cloud providers, and device manufacturers.
This setup is similar to a VNP, where the Access Provider is analogous to the VNP and the Identity Provider is similar to the HSP (Home Service Provider) in mobile networks.
To enable automatic connections, the technology used is Passpoint (802.11u / 802.11i / 802.1x), with a modification to a field called RCOI transmitted via 802.11u.
The RCOI (RCOI field), defined in 802.11u, is used to describe the access policy. This information helps the station (STA) determine if it has the correct Passpoint profile to connect to the network.
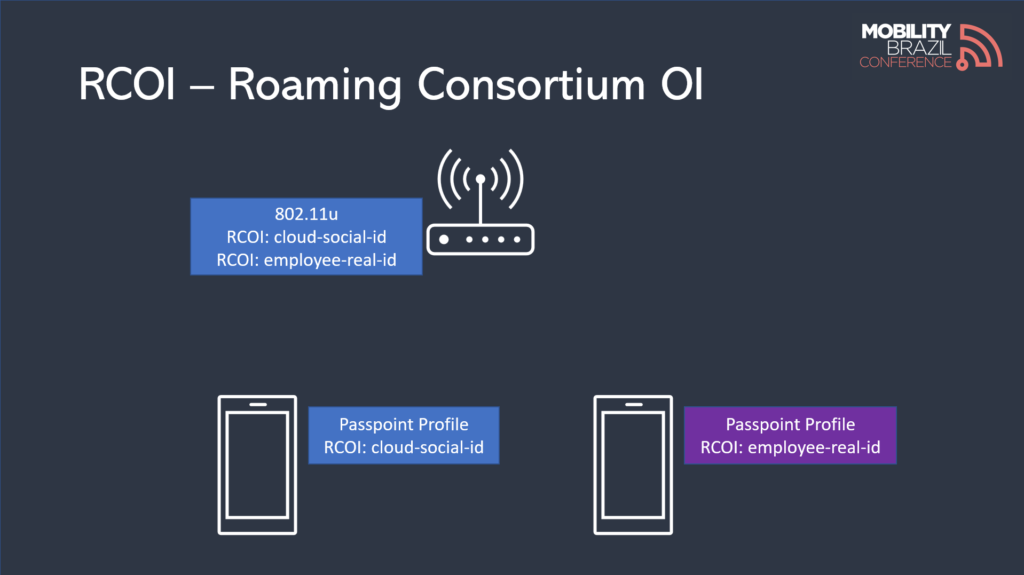
The field provides some important details, such as whether the user’s identity is unique or randomized.
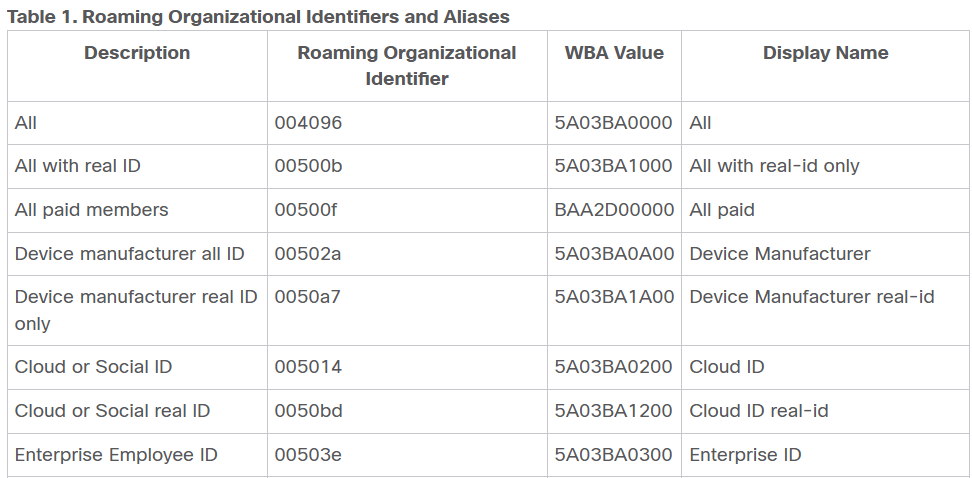
As we’ve seen, WBA has been working with operators for a long time and has developed various standards and best practices for interconnection. Therefore, it is expected that with Open Roaming now under WBA’s control, adoption will increase significantly.
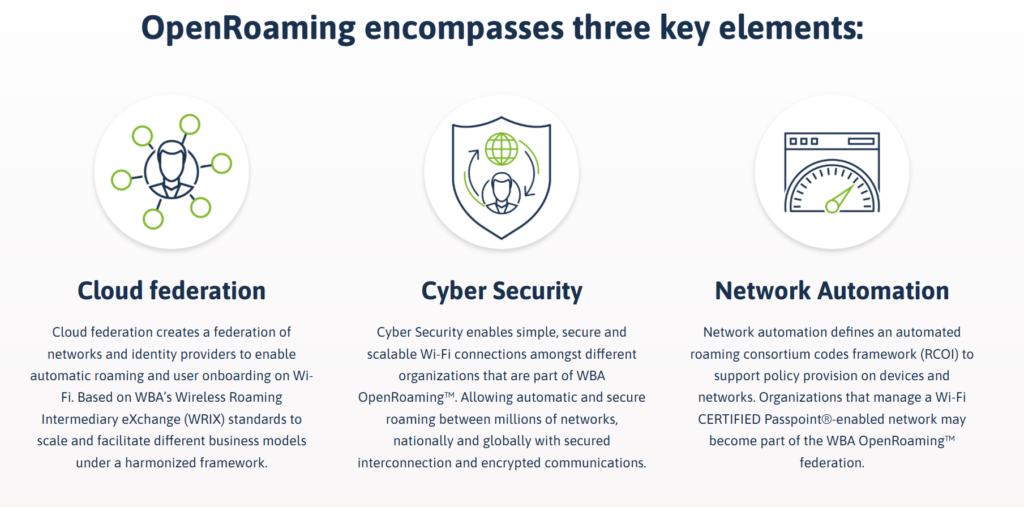
The image below is from the WBA website and highlights the key elements of Open Roaming. We have covered all of these elements, including Passpoint, Radius federation, and WRIX.
To sum up, there are currently several forms of roaming in use, and I don’t think we’ll see just one solution take over anytime soon. What’s really interesting is that with a federated solution like OpenRoaming, companies—and pretty much any identity provider (IDP)—can offer network access and get involved in roaming agreements, not just the operators who have been doing this for years.
In 2021, I gave a presentation at the MBC (Mobility Brazil Conference) on this very same topic, in Portuguese. Feel free to check it out: https://www.youtube.com/watch?v=3plA4L41T5c
Thanks,
Diego Capassi