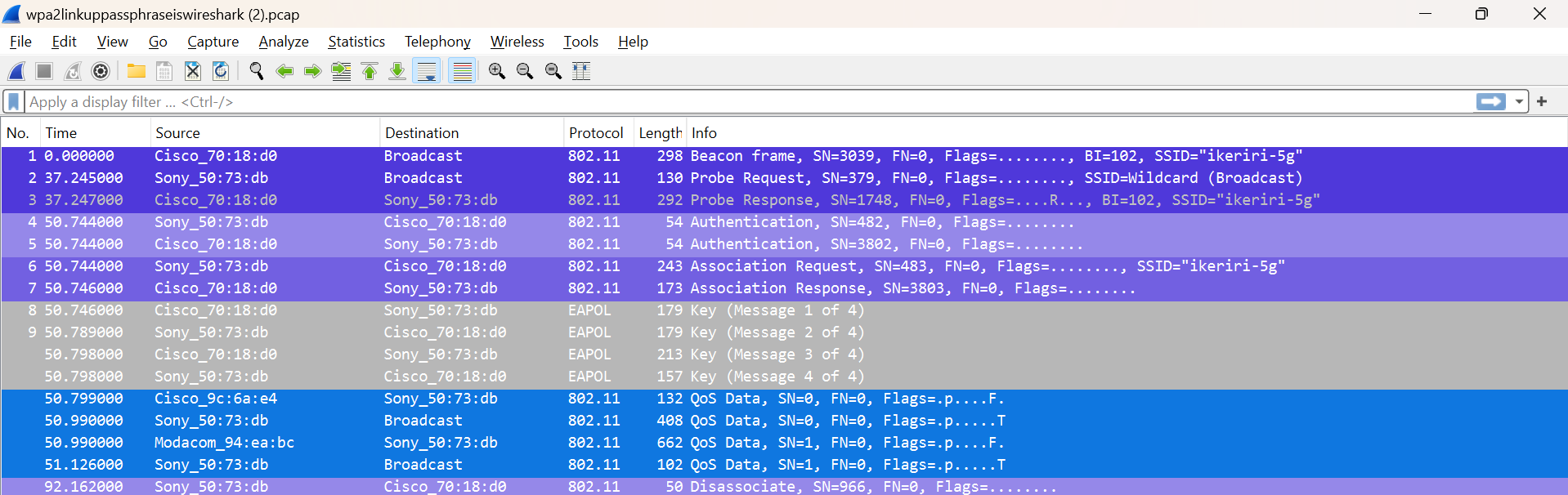
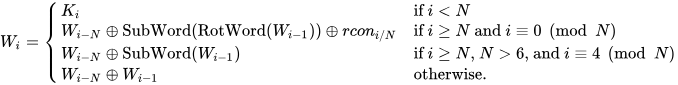In the previous post, we explored the details of the RSNA 4-Way Handshake and key generation. In this post, we’ll focus on decrypting and calculating […]
Tag: encryption
A Deep Dive into RSNA: Key Management and WPA2 Personal Security
802.11i RSN defined the RSNA (Robust Security Network Association), which significantly improved the authentication and encryption mechanisms used in Wi-Fi networks. Prior to RSNA, networks […]
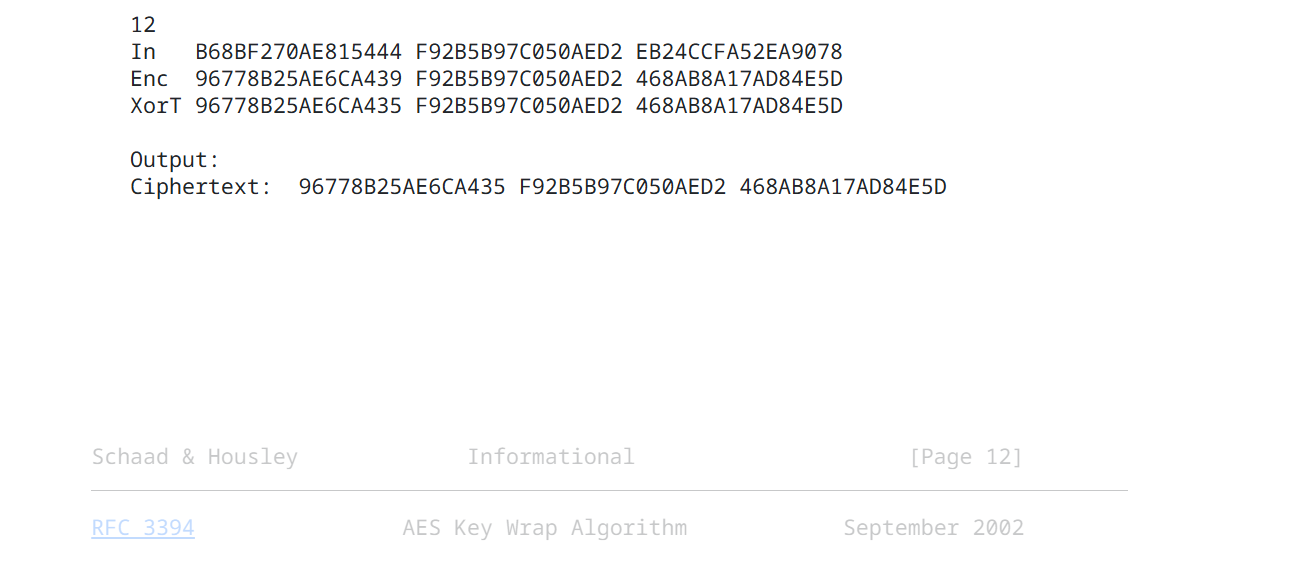
AES Key Wrap: How It Works
When we need to securely send a key, we encrypt it. That’s exactly what AES Key Wrap does—it provides a standardized way to encrypt a […]
Hash Functions in 802.11: HMAC and PRF Explained
Hash functions play a crucial role in various applications, including hash maps, integrity checks, pseudo-random value generation, and transforming a passphrase into a usable key. […]
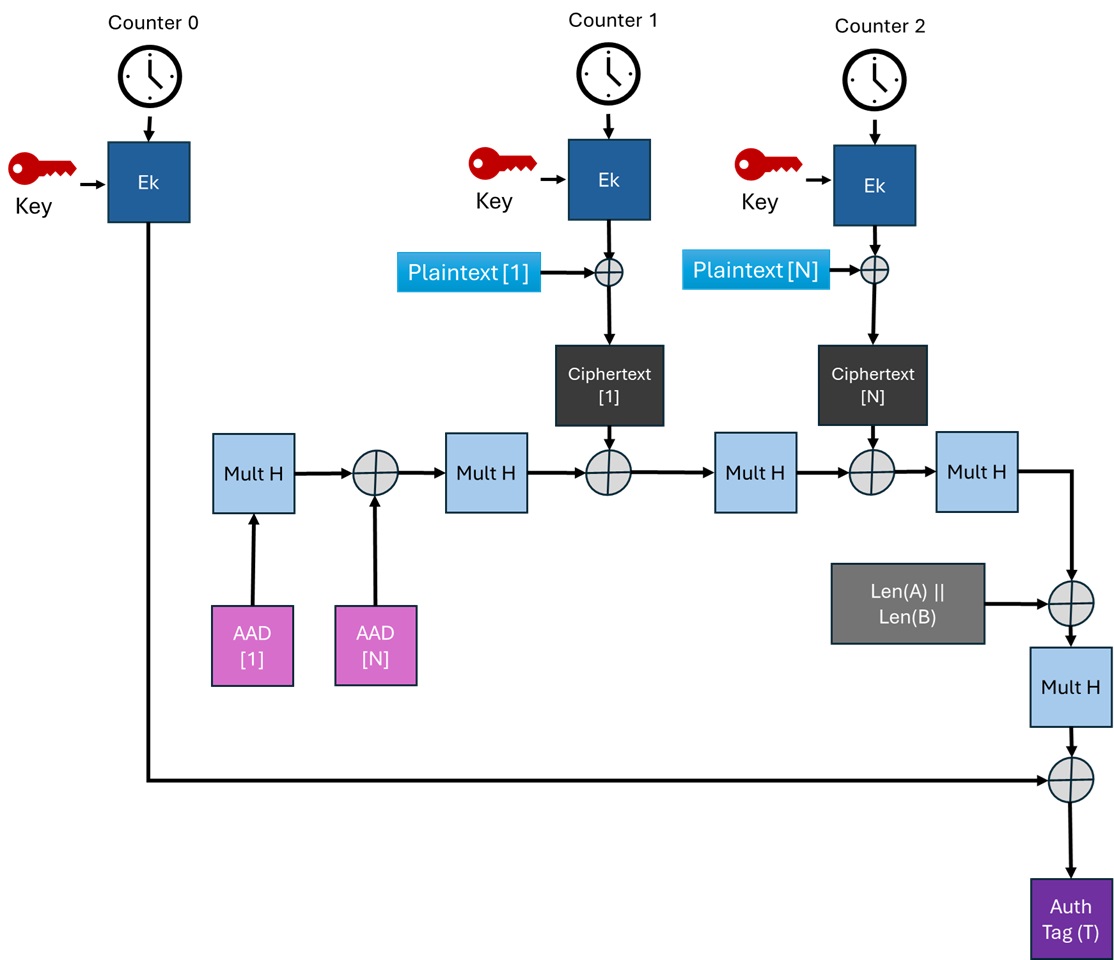
Understanding the Galois/Counter Mode (GCM) Encryption in WPA-3
WPA3 uses advanced encryption techniques to protect data confidentiality and integrity in wireless networks. The encryption method it uses is Galois/Counter Mode (GCM), which enhances […]
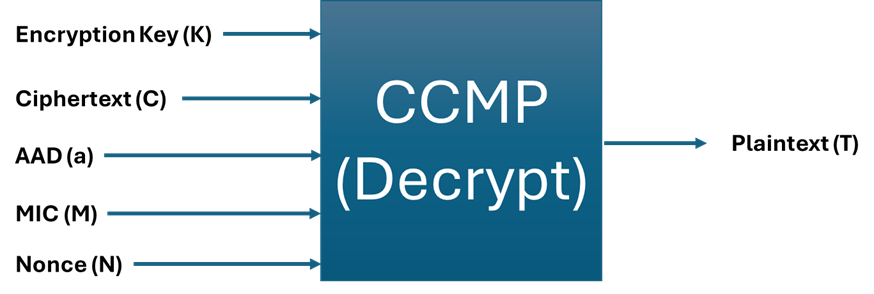
CCM Authenticated Encryption: A Detailed Walkthrough
In my last post, I talked about encryption modes, covering the outdated and not-so-great ECB, along with CBC and CTR. Now let’s dive into CCM […]
Understanding AES Encryption Modes: From ECB to CBC and CTR
In previous posts, we discussed how AES encryption works, breaking down the process of encrypting a 128-bit (16-byte) plaintext into a ciphertext of the same […]
Understanding AES Key Expansion
This post explains how the key expansion process works for AES-128, AES-192, and AES-256. To review some fundamentals: AES is an encryption standard that encrypts […]
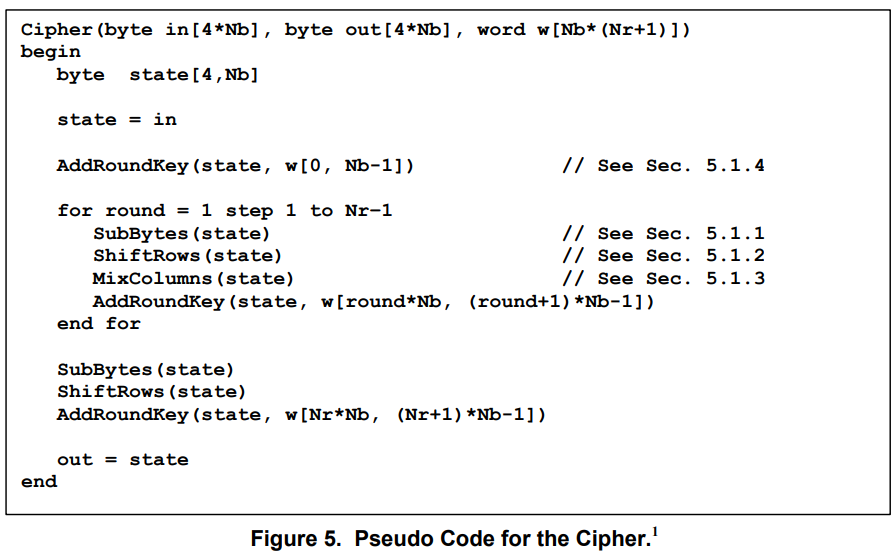
AES-128 Encryption Process: A Step-by-Step Breakdown
One of my favorite acronyms in the industry is CCMP-AES. It’s quite a mouthful: Counter Mode Cipher Block Chaining Message Authentication Code Protocol with Advanced […]